But a lot more than simply concentrating on existing cyber attack trends, which I believe are combined In general, I emphasize these reports to help teach readers the place to go to realize more knowledge and further insights and on knowledge relevant to their industries, as well as certain aids to help you gauge metrics and details bordering these topics.
In combination with cybersecurity engineers, roles such as AI safety analysts, AI architects, and cybersecurity data researchers are emerging as essential positions in corporations.
The future of radio is brilliant and fascinating. As we tactic 2029, radio stations that embrace information and Innovative analytics are going to be most effective positioned to compete with music streaming platforms and captivate their listeners.
Sep 28, 2015 To help make the last 7 days's prime cyber security threats and troubles available to you in a single shot, we are Yet again in this article with our weekly round up. Past week, we came upon lots of cyber protection threats such as the XCodeGhost malware in Apple's Application Shop and lockscreen bypass bug in iOS nine and iOS nine.0.1 that manufactured us unfortunate, but… …we have been also thrilled by hottest developments including Microsoft's new Linux-centered working process Azure Cloud Switch (ACS) , unhackable MicroKernel " SeL4 ", and Facebook ' Dislike or Empathy Button '.
Nonetheless, radio is much from staying a relic on the past. With the strength of details and State-of-the-art analytics, radio is poised to compete and perhaps thrive Within this new era.
Strolling Along with the Pet dog on a brief leash and harness might be a optimistic expertise. Like that, you'll be able to constantly help immediate the animal where by to go.
In the meantime, the median time for detecting the mass exploitations on the CISA KEV on the Internet is 5 times.
1. Ethical Hackers: Often known as "white hat" hackers, moral hackers use their techniques for constructive functions. They help businesses identify and resolve protection vulnerabilities to reinforce their defenses. two. Black Hat Hackers: These hackers have interaction in destructive routines, for example unauthorized entry and information theft, for personal obtain or mischief.
The making has attracted anti-social conduct since it was vacated, resulting in many fires in the last five years.
“There is a wonderful offer at stake for buyers and sellers all across the country, and NAR will keep on to work, out and in of courtroom, toward the absolute best end result for home homeowners in America and the experts who represent them.”
Probably we’re keen on it simply because it feels close to, and it’s humble in its plainness. It’s ours
Whenever your Puppy loses sight progressively, you might need much less re-training and simply move some of the home furnishings all-around, then stroll with the areas with all your Pet dog.
Yes, moral hackers can identify vulnerabilities click here that may make your system susceptible to ransomware and suggest methods. four. Are there legal implications for partaking a real hacker? Partaking an moral hacker for legal and ethical reasons mustn't pose any legal issues. five. How frequently ought to I carry out a cybersecurity audit for my business? It truly is proposed to conduct cybersecurity audits routinely, a minimum of yearly, to guarantee ongoing security.
If you would like help knowledge what It truly is like caring to get a diabetic Doggy, look into this weblog. Excitement, the Diabetic Puppy is a superb resource.
 Jennifer Grey Then & Now!
Jennifer Grey Then & Now! Mr. T Then & Now!
Mr. T Then & Now!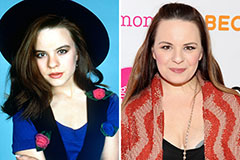 Jenna Von Oy Then & Now!
Jenna Von Oy Then & Now! Keshia Knight Pulliam Then & Now!
Keshia Knight Pulliam Then & Now! Pierce Brosnan Then & Now!
Pierce Brosnan Then & Now!